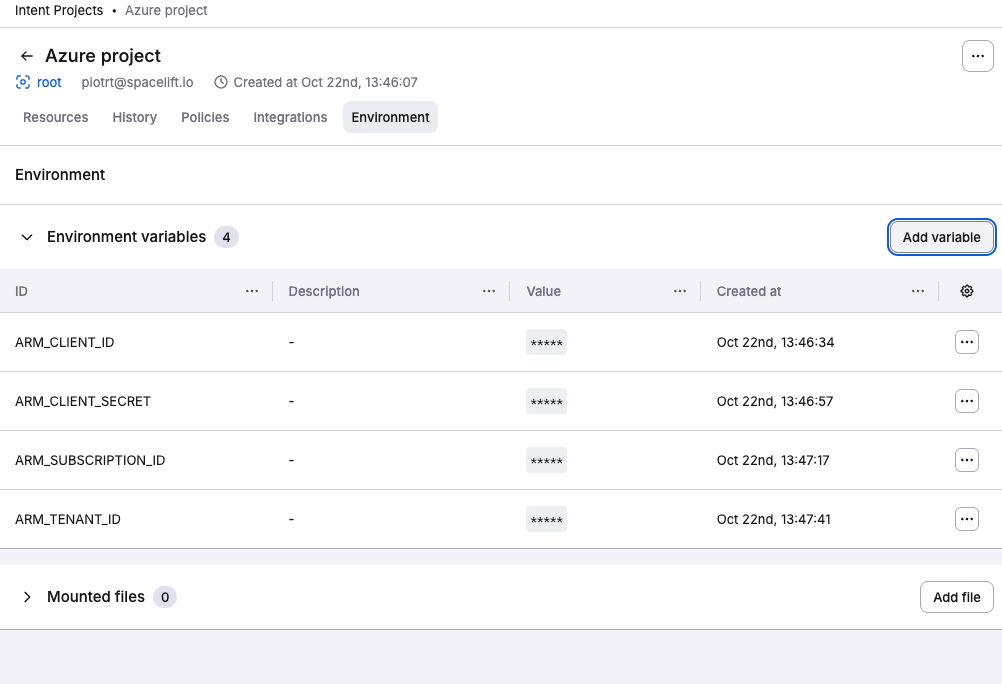
Setting up Azure and GCP credentials for Spacelift Intent»
Azure credentials»
-
Get your tenant id.
1 2
$ az account show --query 'tenantId'` "<YOUR-TENANT-ID>" -
Get your subscription id.
1 2
$ az account subscription list --query '[].{name:displayName,id:id}' [ ... , { "id": "<YOUR-SUBSCRIPTION-ID>", "name": "..." }, ... ] -
Optionally, create a role (role.json).
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16
{ "Name": "example-role”, "IsCustom": true, "Description": "example-role", "Actions": [ "Microsoft.Resources/subscriptions/<ACTIONS…>" ], "NotActions": [], "DataActions": [], "NotDataActions": [], "AssignableScopes": [ "/subscriptions/<YOUR-SUBSCRIPTION-ID>" ] } $ az role definition create --role-definition role.json -
Create a service principal.
1 2 3 4 5 6 7
$ az ad sp create-for-rbac --name "example-name" --role "example-role" --scopes "/subscriptions/<YOUR-SUBSCRIPTION-ID>" { "appId": "<YOUR-CLIENT-ID>", "displayName": "example-name", "password": "<YOUR-CLIENT-PASSWORD>", "tenant": "<YOUR-TENANT-ID>" } -
Get client id and client password from above and setup env vars.
1 2 3 4
ARM_CLIENT_ID="<YOUR-CLIENT-ID>" ARM_CLIENT_SECRET="<YOUR-CLIENT-PASSWORD>" ARM_TENANT_ID="<YOUR-TENANT-ID>" ARM_SUBSCRIPTION_ID="<YOUR-SUBSCRIPTION-ID>"
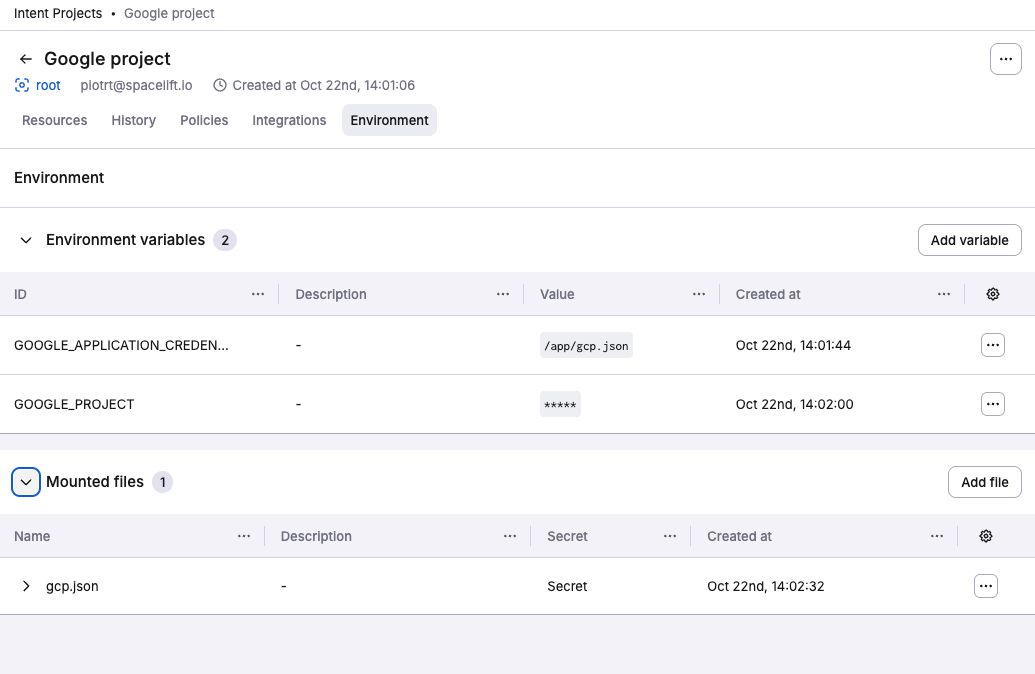
Google credentials»
Configuring Google credentials for Intent follows the same steps as setting up GCP for Spacelift, with only a slight change to the file paths for spacelift.oidc and gcp.json.
-
When setting up the OIDC file location, use
/app/spacelift.oidcinstead of/mnt/workspace/spacelift.oidc.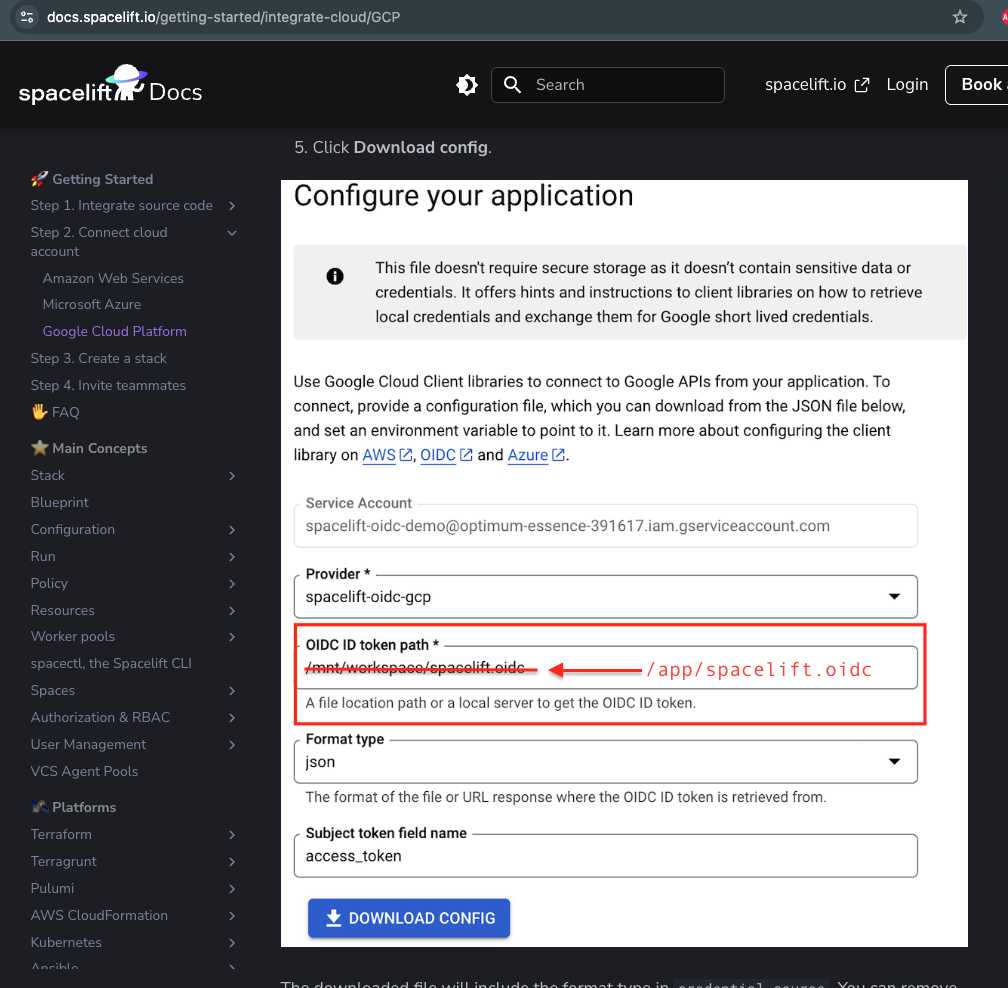
-
When setting up the JSON configuration, use
/app/spacelift.oidcas well.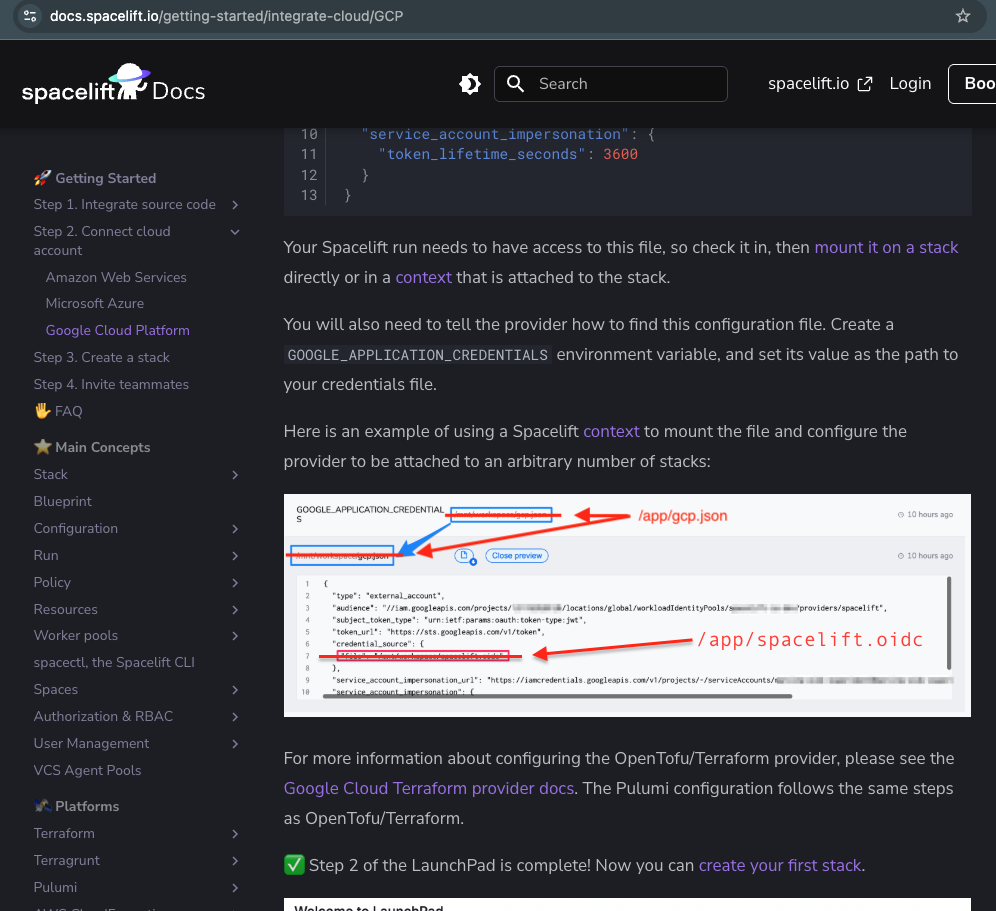
-
At the end we need:
GOOGLE_APPLICATION_CREDENTIALS=<pointing-to-JSON-configuration-file>.GOOGLE_PROJECT=<project name>(optional).gcp.json(JSON configuration file).spacelift.oidcwill be automatically mounted.